Table of Contents
- The Hidden “Security Tax”: The True Cost of a Fragmented Model
- Security by Design: The FortiToken Alternative
- Defguard in Practice: The Prusa Research Case
- The Real Choice: A Fragmented Model vs. A Unified Foundation
- Frequently Asked Questions (FAQ)
To comply with standards like NIS2, Multi-Factor Authentication (MFA) has become a baseline requirement, not an option.
Yet in most enterprise VPNs, fundamentals such as MFA, SSO, and identity management are still treated as extras; not for technical reasons, but because separating them is profitable.
The result is predictable: organizations end up buying their security in fragments just to meet compliance. This leads to increased Total Operating Costs and time lost on stitching MFA and VPN together.
The problem isn’t technical; it’s commercial. Vendors have learned to turn essential protection into a series of recurring upgrades.
This article breaks down how that model works — and how Defguard was designed to solve it.
The Hidden “Security Tax”: The True Cost of a Fragmented Model
When basic security requirement is sold as a separate product, expenses rise fast — not just in licensing, but in complexity and risk.
1. The Licensing Cost
The “security tax” is unpredictable. The appliance price looks reasonable, but then you must add per-user MFA tokens and SSO or identity module licenses. The cost keeps scaling with your headcount, not your security.
2. The Operational Cost
This is the pain system admins feel. Every add-on, like separate MFA modules or token licenses, adds more components to configure, maintain, and update. Each new piece introduces another integration point, another dependency, and another potential failure.
Our Fix:
Defguard runs as a single, unified platform, ready to deploy in minutes and built to integrate with your existing environment.
From one admin panel, you can manage users, groups, devices, and MFA settings, define access policies, and monitor connections, all without switching between tools.
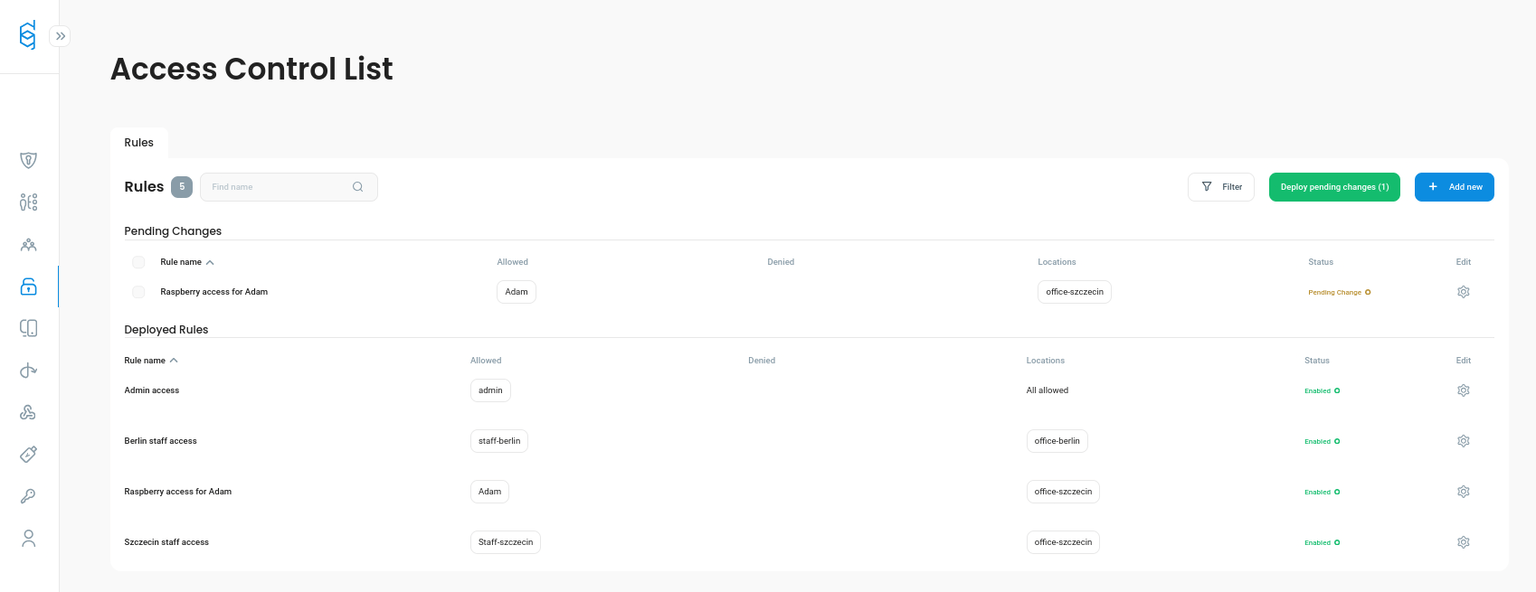 All security layers in one place — users, devices, MFA policies, and access rules.
All security layers in one place — users, devices, MFA policies, and access rules.
3. When Security Becomes Optional
The real risk? Because MFA is a separate purchase, some departments may skip it to save budget. That creates inconsistent protection — the exact kind of compliance gap auditors find and attackers exploit.
Our Fix:
In Defguard, MFA isn’t a license you can skip, it’s part of the core platform. You cannot have a compliance gap when the secure baseline is the only baseline.
Security by Design: The FortiToken Alternative
We believe the legacy model is broken. Security isn’t something you add — it’s something you build on.
A modern VPN shouldn’t upsell you MFA; it should deliver it by design. That’s the principle behind Defguard.
How We Do It: A Unified Platform
Defguard is a self-hosted, unified solution where identity and access control are part of the same architecture. Here’s what that means in practice:
1. Built-in User Management (IdP)
Defguard includes a native user database — often referred to as an Identity Provider (IdP) — as a core service. It lets you manage users and groups directly, without premium extensions or add-ons, and can act as an SSO provider for your organization.
2. Built-in Multi-Factor Authentication (MFA)
Defguard also handles MFA as a core service, supporting standard time-based one-time passwords (TOTP) from authenticator apps such as Google Authenticator or Microsoft Authenticator — no proprietary tokens required. You can explore Defguard’s built-in MFA to see how it integrates seamlessly into your existing security environment.
3. Integration with Your Existing Tools
Defguard natively integrates with identity systems like Microsoft Entra ID, Google Workspace, Okta, and JumpCloud using the standard OpenID Connect (OIDC) protocol. This allows users to log in with their existing accounts while keeping authentication consistent and secure across your entire infrastructure.
 Unified architecture — one core, one proxy, multiple locations.
Unified architecture — one core, one proxy, multiple locations.
The Proof: It’s in Our Open Source Plan
These security capabilities are not tiered upsells. The ultimate proof is in our design: our Open Source plan includes both the built-in user database (IdP) and connection-level MFA from the start.
This is the difference between a system built for monetization and one built for security — where essential protection is always included, and scale comes from context, not paywalls.
Defguard in Practice: The Prusa Research Case
This isn’t theoretical. Prusa Research needed to scale their VPN for over 500 users, including production-floor devices and remote employees.
A fragmented model would have forced them to manage hundreds of separate token licenses and deal with complex identity integrations. This was not a scalable or efficient solution.
How we solved their problem:
They chose Defguard because it’s a single, unified platform. Because MFA is built-in, there are no token licenses to manage. Their IT team can provision a new user with MFA enabled in seconds, all from one place. When a user connects, Defguard enforces MFA as part of the connection process itself.
The outcome is simple:
100% of their VPN users have MFA enabled, because MFA isn’t a license you can skip, it’s part of the core platform.
The Real Choice: A Fragmented Model vs. A Unified Foundation
The problem with the legacy model is clear: you are forced to pay an enormous extra cost for MFA just to be compliant. This isn’t an accident. It’s the result of a business model designed to sell you security in separate, expensive pieces. Legacy VPNs treat security as a catalog of features; Defguard treats it as a foundation.
If you’re facing another license renewal and see a “security tax” on your invoice, maybe it’s time to move from a fragmented solution to a foundational one.
See what built-in security looks like.
Book a Demo and explore Defguard’s modern VPN with MFA included.
Frequently Asked Questions (FAQ)
How much does Fortinet MFA cost?
Fortinet’s MFA isn’t a single price. It often requires separate purchases like FortiToken (for MFA) and FortiAuthenticator (for identity).
These components are necessary for compliance and make the true TCO much higher than the base price.
Is FortiToken required for Fortinet VPN MFA?
Yes. In most FortiGate VPN configurations, FortiToken is the required component to enable MFA — as hardware or mobile tokens, licensed per user.
What is a good FortiToken alternative?
A modern alternative to token-based MFA systems. Defguard includes Multi-Factor Authentication as a built-in feature — supporting standard TOTP codes from authenticator apps (like Google Authenticator) and a native user database (IdP) in every deployment. Learn more about Defguard VPN with built-in MFA.
Are there VPNs with MFA included in the base price?
Yes. Defguard, as a modern WireGuard®-based platform, includes MFA by default — built into every deployment, with no extra licensing or modules.