Desktop and Mobile Clients
Stay secure, whether you're on desktop (Linux, macOS, Windows) or on the go with Android or iOS.
The Defguard Mobile VPN Client is here - now alongside our desktop apps — bringing secure, zero-trust networking to all your devices.
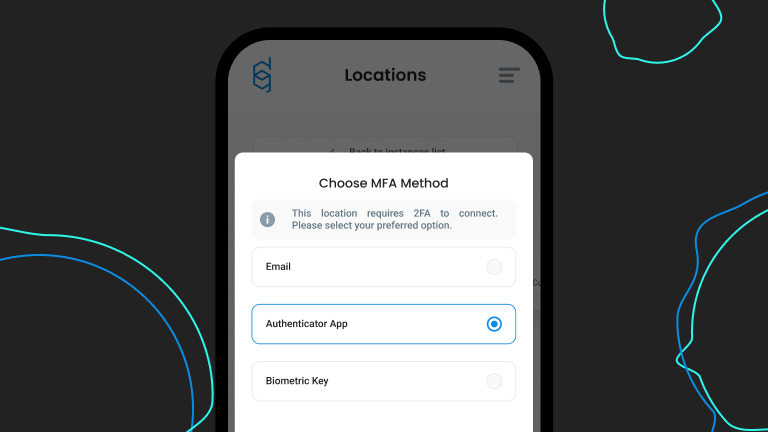
- True 2FA/Multi-Factor Authentication on WireGuard® with Biometrics
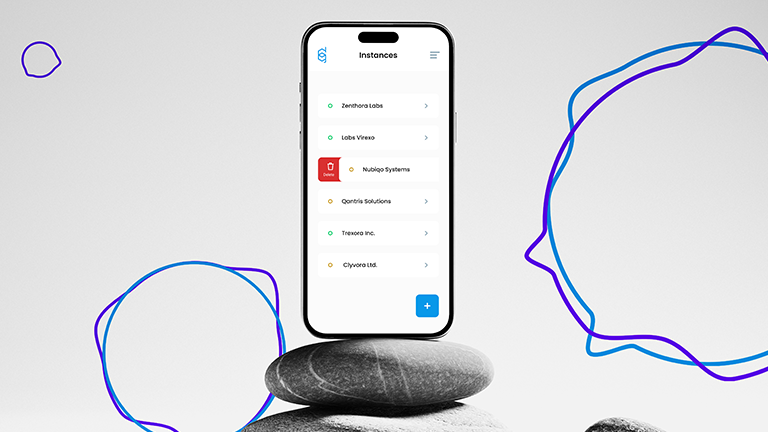
- Multiple instances and VPN locations in one client
- Instant VPN configuration updates and flexible client management
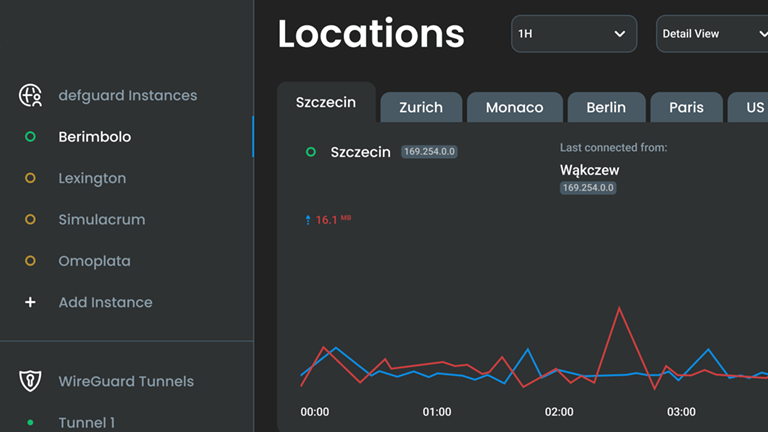
Multiple instances and VPN locations in one client
Defguard is uniquely designed for MSPs, cloud providers, and data centers. It allows deployment of multiple isolated Defguard instances (for different clients, sites, etc.) while maintaining unified access through a single desktop app.
Now available on mobile!
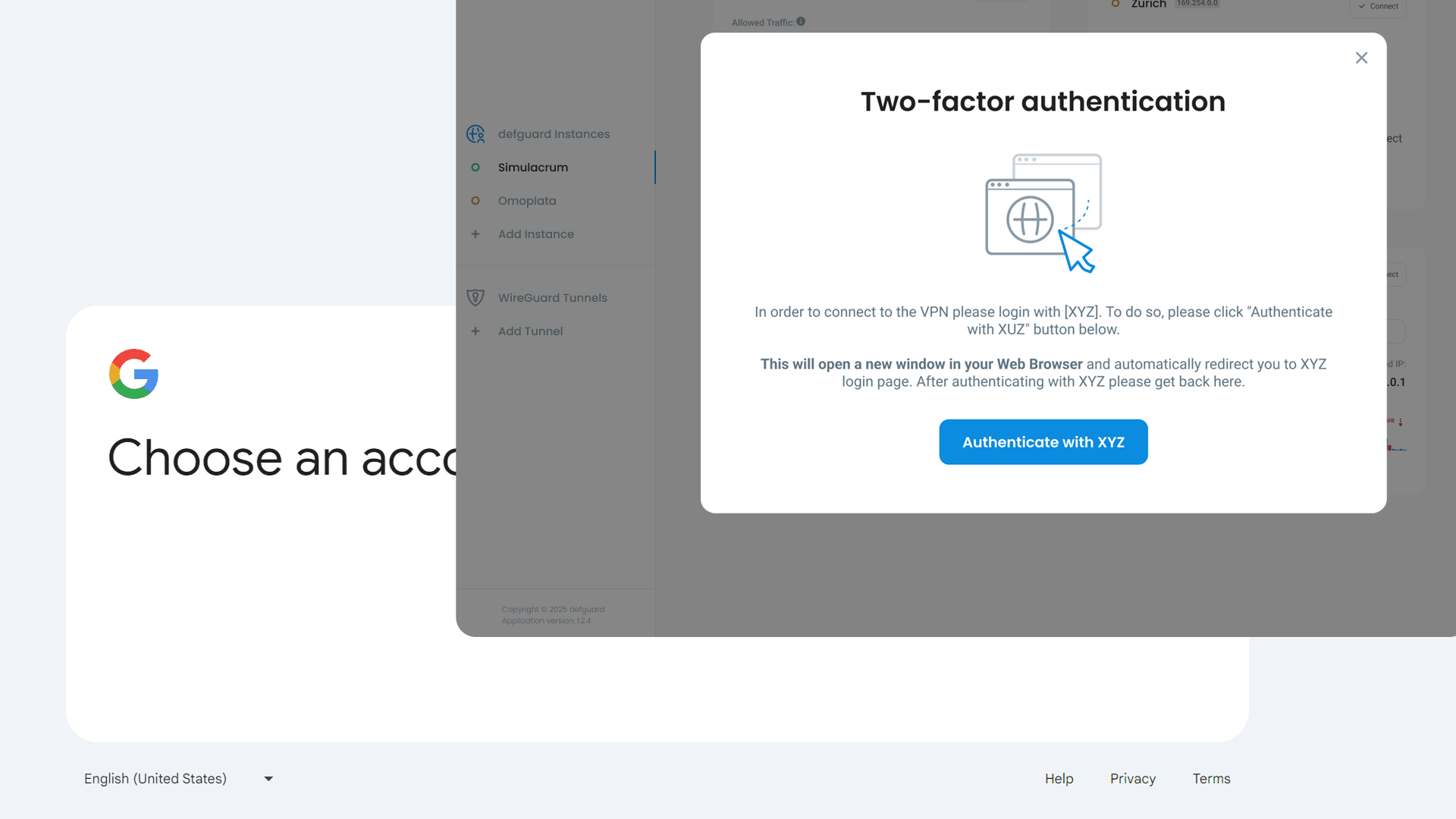
True 2FA/Multi-Factor authentication on WireGuard®
Both desktop and mobile clients supports both Defguard internal Multi-Factor Authentication and external SSO (Google/Microsoft/Otka/others) MFA.
Now available on mobile
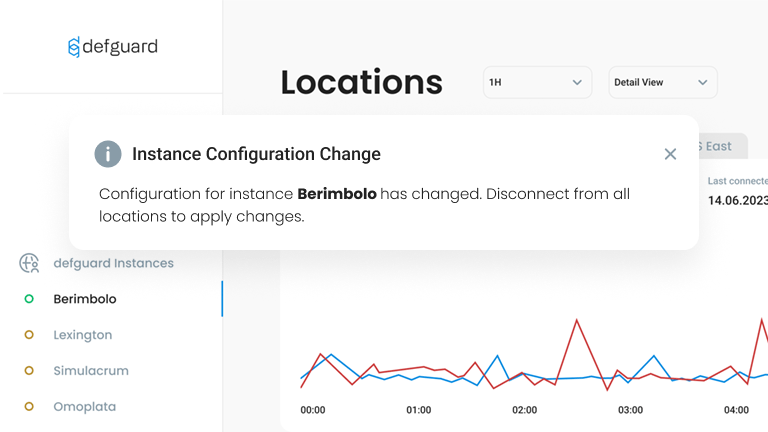
Instant VPN configuration updates and flexible client management
Defguard enables real-time synchronization and configuration of client applications used by users. Any changes in VPN configuration or access management are immediately reflected on the user side. Additionally, it allows managing client behavior (e.g., enabling full traffic routing through the VPN or blocking certain features of the client).
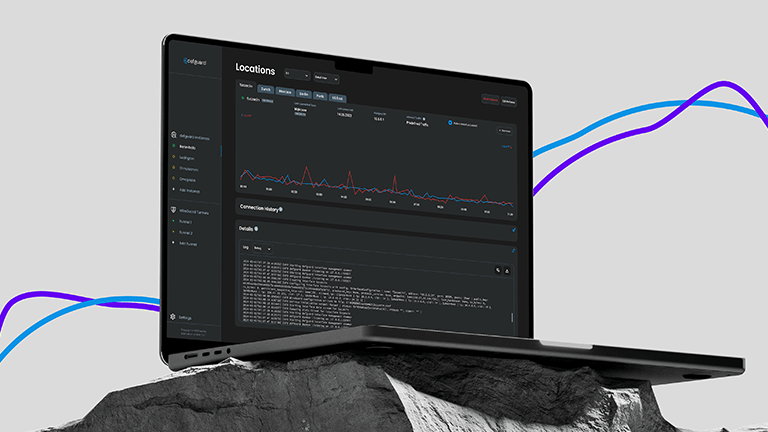
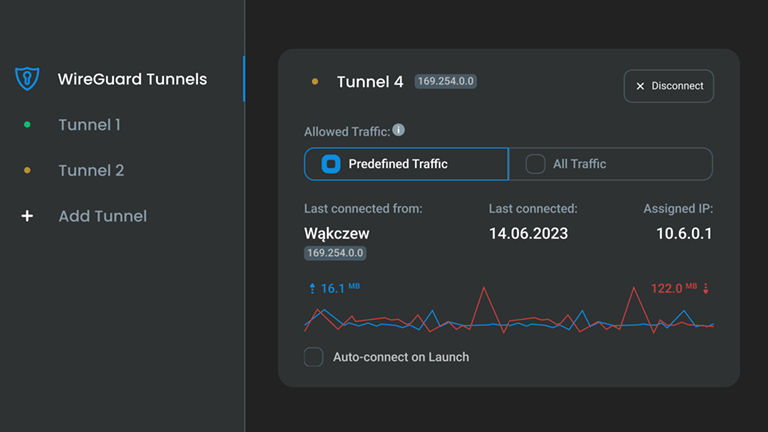
Detailed connection overview
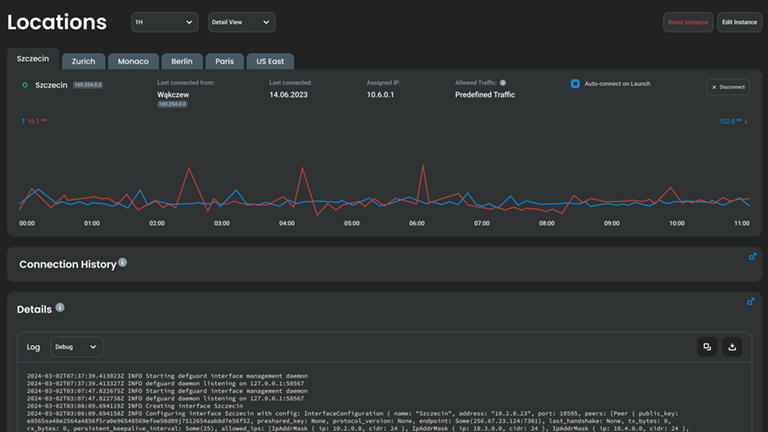
Each connection can be tracked with detailed statistics, logs and tunnel details (IPs, ports, DNS settings, routing tables)
Multiplatform and Multi architecture
Available form macOS, Windows and Linux (Ubuntu/Arch/RPMs) and Intel/ARM architectures.

Any WireGuard® server is supported
- Not only Defguard instances but any WireGuard® server is supported - just import (by wizard) your current configuration and use Defguard client with your current setup!
- Note: that only Defguard instances (combined with Defguard server) enables 2FA/Multi-Factor support.
Ready to Implement Enterprise-Grade WireGuard® VPN?
See how Defguard fits into your zero-trust architecture and existing infrastructure.